What is zero trust architecture (ZTA)? Pillars of zero trust and trends for 2024
As the threat landscape continues to evolve, tightening cybersecurity has become increasingly important, both for internal operations and end-user experiences. With so many more people and systems interacting with digital assets, improving the security of these connections has become a top priority for organizations.
Learn Network Security Fundamentals
![]()
This is where zero trust architecture (ZTA) has come to play a significant role because it helps keep data, applications, and networks safer by safeguarding them against threat actors that try to access them. ZTA involves presuming that every entity trying to connect to a network or application is a threat. In the context of cybersecurity in 2024, ZTA provides the level of protection that digitally transformed infrastructures need to avoid costly attacks and outages.
Zero trust architecture explained
ZTA is an approach to security based on the concept of "never trust, always verify." It involves presuming that every single device, user, or application that tries to connect to digital assets is a threat. And until the entity can prove otherwise, the system doesn't allow it to interface with the asset.
Zero trust architecture was first conceptualized in 2010 by John Kindervag. He suggested that the traditional security model was inadequate to protect from modern threats. His approach represented a fundamental shift in how organizations defended their infrastructures. Traditionally, a company would view internal digital assets within their network as at least somewhat trustworthy while being more suspicious of people and devices outside of their internal networks. By following ZTA, organizations view all connections, regardless of whether they originate from, as potential threats. In other words, they "never trust" an entity and "always verify" its legitimacy before allowing access.
The principles of zero trust
ZTA is built on a few core principles that, when used together, foster more secure networks:
-
Identity verification. To verify identities in a ZTA-based system, you typically use multifactor authentication. This requires more than one piece of evidence to demonstrate the authenticity of the personal system trying to connect.
-
Device trust. By incorporating device trust principles, you ensure that each endpoint that connects to your network is trustworthy as opposed to an attacker using a weapon.
-
Network segmentation. Network segmentation focuses on dividing networks into different sections and then protecting them individually. One benefit of this technique is that it can prevent an attack from moving laterally between two segments of your network. It also shrinks the surfaces security teams must defend, simplifying your security solution.
-
Policy enforcement. Policy enforcement in the context of ZTA involves dynamic access controls that you can change according to shifting needs. It also incorporates context-aware access controls, which can limit access based on a pre-designed set of factors at the time of connection.
Zero trust and the modern cybersecurity ecosystem
ZTA has played a particularly important role as more and more organizations have shifted to cloud services and infrastructure. Since a cloud-provided service could be compromised by a threat actor, endangering potentially large communities of stakeholders, ZTA has added a level of stringency that many organizations now depend on.
For example, a company that uses a cloud-based customer relationship management (CRM) solution may need to secure thousands of customer profiles used by hundreds of employees. By presuming that even internal employees and devices are threats, these kinds of organizations reduce the chances of insider attacks impacting the data privacy of customers.
ZTA provides a similarly elevated level of protection for remote and hybrid work models. For instance, if a remote employee safely accesses their company's virtual private network on Thursday, a ZTA-based system won't presume their device is safe when they try to connect again on Friday. This prevents an attacker who has stolen a laptop or a phone from exploiting previous, trusted connections.
The security boost that ZTA provides also makes it easier to comply with regulatory legislation regarding data privacy. For instance, some compliance measures require that sensitive data can only be seen by certain qualified persons. Using ZTA, you can verify the identity of each person who tries to connect every time they attempt to access this data.
Learn Network Security Fundamentals
![]()
Implementing zero trust in an organization
To transition to a zero trust architecture in your organization, you can follow these measures:
-
Identify the data, applications and assets you need to protect, mapping these out according to their locations within your campus, in the cloud or in various remote locations.
-
Map out the dependencies and clearly outline the relationships with the assets identified in step one.
-
Separate data into different classes, categorizing it according to how sensitive or business-critical it is
-
Implement authentication mechanisms such as multifactor authentication to make sure each user is thoroughly vetted before they're allowed to access a system.
-
Segment your network, isolating different sections from each other so a threat can't move from east to west.
-
Ensure you have full visibility into every user and device that connects to your network and the different types of traffic that flow through it.
-
Ensure that all data moving through the network is encrypted, including when it's being stored.
-
Establish a system for continuously monitoring your zero-trust architecture and use it to adapt to any network adjustments or technological advancements.
Even if you use these techniques to establish a ZTA system, you may come across a few challenges during the implementation process. For example, you must source the technology needed to set up multi-factor authentication, as well as make sure internal and external users are comfortable with it.
Deciding how to segment your network can also be difficult because some services or applications may be tightly integrated, and siloing their data could impact workflows.
Also, if your business uses hybrid or remote work models, you must set up a system that enables new or transitioning employees the access they need without adding unnecessary friction. For some organizations, this may require having someone on hand to provide support for new users or those with changing roles.
The Pentagon's approach to zero trust
The move to ZTA may take a while for organizations to fully implement. For example, the Pentagon publicly released its Zero Trust Strategy and Roadmap in November 2022, and in May 2023, the DOD's deputy chief information officer, David McKeown, said that the DoD is on track to implement the zero trust framework by fiscal year 2027.
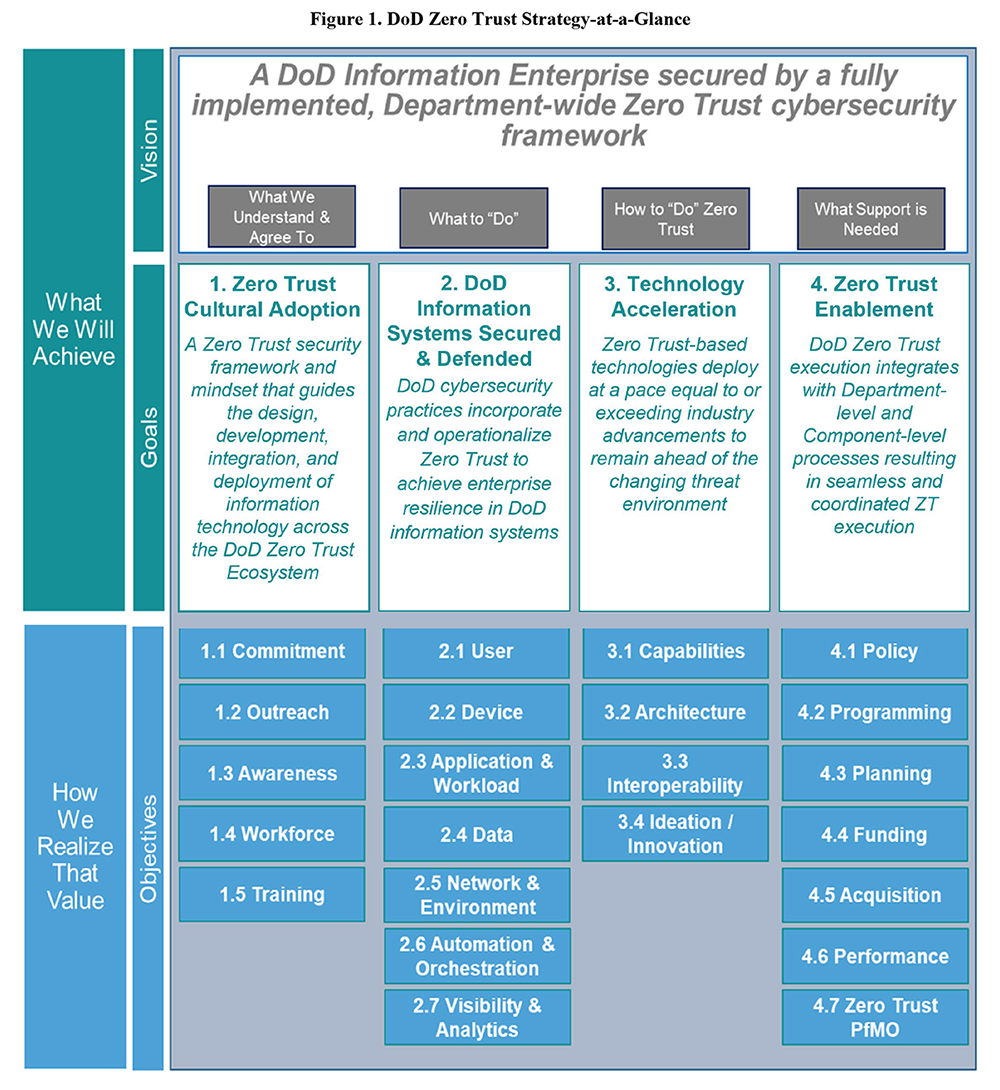
The Pentagon's lengthy path to a "fully implemented, department-wide zero trust cybersecurity framework" includes four pillars:
1. Zero trust cultural adoption: A zero trust security framework and mindset that guides the design, development, integration and deployment of information technology across the DoD zero trust ecosystem.
2. DoD information systems secured and defended: DoD cybersecurity practices incorporate and operationalize zero trust to achieve enterprise resilience in DoD systems.
3. Technology acceleration: Zero trust-based technologies deploy at a peace equal to or exceeding industry advancements to remain ahead of the changing threat environment.
4. Zero trust enablement: DoD zero trust execution integrates with department-level processes resulting in seamless and coordinated zero trust execution.
Zero trust in action: Use cases and applications
Even though zero trust architecture has many potential applications, here are some of the most common:
-
Protecting against phishing and social engineering attacks. Because ZTA requires multiple authentication credentials before enabling access, even if a phishing attacker steals a username and password, they may still be unable to break through your defenses.
-
Preventing lateral movement within networks. When you use network segmentation, an attacker who gains access to one portion of your network will have to re-authenticate to gain access to other sections. This limits the amount of damage they can do.
-
Securing multi-cloud and hybrid environments. Network boundaries aren't always clear from a security perspective in a multi-cloud or hybrid environment. But ZTA uses identity-based security, so it doesn't matter which network someone is accessing; it's their identity that the system focuses on.
The future of zero trust architecture
In 2024, ZTA is poised to play an even more significant role in helping companies secure their infrastructures. As more organizations transition to cloud-based services, the demand for ZTA will increase. This is especially true because it needs to be able to protect a cloud-based environment from users logging in from unpredictable locations.
In addition, systems that work in the cloud often interface with other programs that use their data. You need ZTA to make sure that each connection used to exchange data is legitimate. Otherwise, hackers could use fraudulent devices or software to steal information that only trusted technologies should have access to.
AI and machine learning can also play an important role in the future of ZTA. You can use machine learning to analyze behavior on a network, such as how often users connect and from where. The machine learning system can then analyze the data and determine which connections are most likely safe and present significant risk.
Given the strength that ZTA principles bring to security systems, it's also likely that regulators will incorporate them into future compliance requirements. For instance, ZTA could bolster security in the financial sector if people were always required to present multiple forms of identification when withdrawing funds.
Challenges and criticisms of zero trust
Several misconceptions about zero trust can lead some to shy away from relying on it. Some think ZTA is limited to a single security technique, such as one their organization is considering using. For instance, if a company is considering using network segmentation, people may refer to that as "zero-trust architecture" when that’s just one of several ZTA techniques. Because of this, they may not understand the depth of benefits of the full gamut of ZTA initiatives.
Others may feel that adopting ZTA would force them to completely overhaul their security infrastructure. However, they can implement ZTA step-by-step, slowly growing their program as people get used to new access and security protocols.
One of the dominant concerns facing zero trust architects is how it impacts the user experience. Employees and end-users who are used to quickly logging in simply with a username and password may balk at adding at least one more element of proof each time they connect. Also, some may feel that if they just accessed a system the day before, they should be granted leeway as they log in again. This can lead to user frustration for internal stakeholders and customers a business serves.
Productivity is another concern because, in some situations, ZTA can prevent people from being able to work at all. For example, suppose your company has a Microsoft 365 account, which you use to access and work with Excel spreadsheets.
Not realizing your phone is on your lap, you step out of your car and hear it hit the ground with a crack — and a quiet splash. Your phone's ruined, taking your productivity along with it. You can't log into 365 because you need a username, password, and the authentication app on your phone. From the perspective of 365's ZTA-based system, you're not someone whose phone slipped into a puddle; you're a hacker who's stolen a username and password.
Learn Network Security Fundamentals
![]()
This is why it's important to balance security with user experience. It's often better to have a more flexible ZTA infrastructure, especially when authenticating identities. For example, you can offer users three or four options for verifying their identities in an MFA system. They could use their username and password with an authentication app, fingerprint scan, or a one-time access code sent through email.
ZTA also must pivot to meet new threats head-on. For example, attackers could use AI to trick a ZTA system that detects anomalous device behavior. A hacker could figure out the attributes the system looks for as it tries to detect suspicious login attempts, such as attempts from IP addresses connected with specific geographical locations. The attacker could then leverage AI to change the IP address of the machine trying to hack the system each time it attacks — only using IP addresses associated with approved cities, states, and countries.
The importance of zero trust architecture
Despite some of its criticisms and challenges, ZTA cybersecurity is a step in the right direction for companies that want to protect their networks. It presumes every entity is an attacker, forcing people, devices and networks to verify their legitimacy before gaining access. In this way, ZTA can significantly reduce the number of successful attacks stemming from stolen devices or credentials. ZTA can also help contain malware and cybercriminals that try to move laterally once inside a network.
It's best to be proactive as you adopt and refine your ZTA strategies. This is essential if you want to overcome the challenges and criticisms outlined above, as well as continually tighten your security system over time.
To learn more about zero trust, check out Infosec's Fundamentals of Zero Trust Learning Path.







